At Pax8, we prioritise cybersecurity. This is why we advise our managed service provider (MSP) partners to implement the Center for Internet Security’s (CIS) Critical Security Controls, a comprehensive global framework featuring straightforward best practices for cybersecurity. This framework also addresses the security standards used in Europe, the Middle East and Africa (EMEA). In this blog, we’ll cover what the CIS Controls are, how they correspond to security standards specific to the EMEA region, and how Pax8 can help our partners around the globe implement the security measures involved.
Why cybersecurity is so important
Cybersecurity incidents are growing around the world, and this issue is particularly challenging in the EMEA region. Deloitte has found that EMEA faces more cybersecurity incidents than both the Asia-Pacific region and the Americas, with 20% of respondents in the region experiencing 11 or more incidents a year. And the global average cost of a data breach rose to $4.45 million in 2023.
Given this landscape, the cybersecurity market is booming across the globe. In EMEA alone, it’s projected to reach $51.53 billion in 2024. This means that clients are paying attention to who can serve their security needs, and MSPs must be ready to respond with a framework that provides best practices for cybersecurity planning and execution.
What are the CIS Critical Security Controls?
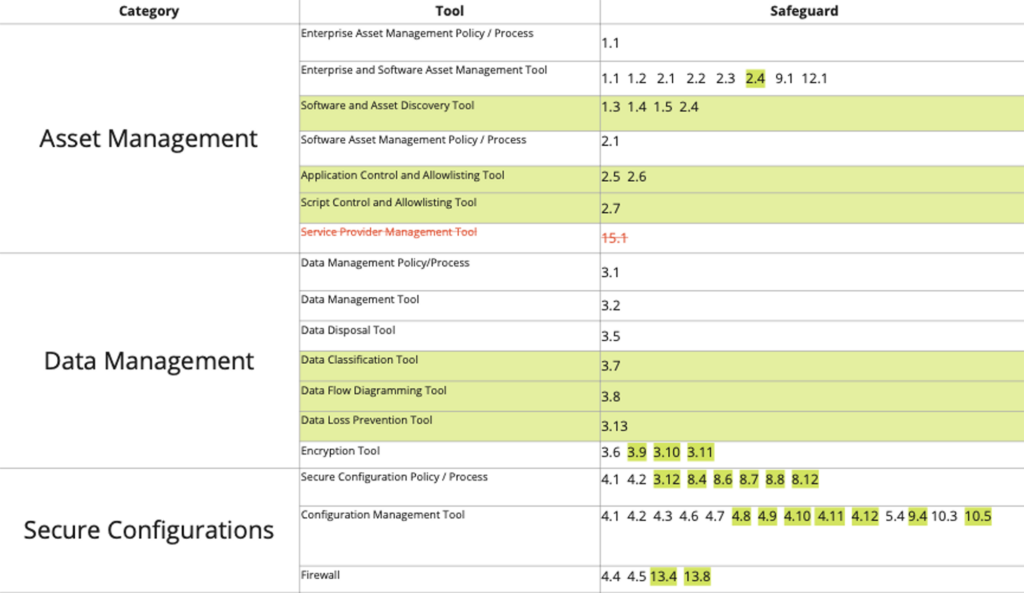
This framework consists of 18 Controls that range from malware defence to managing incidents when they do occur. These controls are also broken down into 153 safeguards that go into more detail about each of the Controls.
Pax8 advocates for adhering to the CIS Controls because they constitute one of the most comprehensive and robust cybersecurity frameworks available. The CIS Controls offer extensive coverage across all critical areas of cybersecurity, ensuring a thorough and effective approach to protecting systems and data. This framework also adheres to global security standards, including those specific to the EMEA region and various industry requirements, which enhances its relevance and applicability across diverse environments.
While the fundamental principles outlined by the CIS Controls provide substantial guidance for MSPs aiming to enhance their clients’ cybersecurity, implementing each Control and its safeguards can be challenging. To assist with this, we collaborated with the Center for Internet Security® (CIS) and more than 30 contributors from the global MSP community to create the “CIS Controls Handbook: A Visual Guide to Evaluating Cybersecurity.” This handbook details each of the CIS Controls and offers a thorough evaluation of their components.
To see how each of the Controls is mapped out, view the chart below:
In addition, you can watch our video walkthrough to learn more.
What are the security standards local to the EMEA region?
Adopting CIS Controls enhances the security protocols you or your clients may already be acquainted with in EMEA, to help ensure compliance with both regional and industry-specific standards that are essential for operational integrity. Listed below are examples of commonly known security frameworks in EMEA that align with CIS Controls. These local frameworks, while diverse, share common goals with CIS Controls in establishing robust security practices:
Cyber Essentials
Cyber Essentials is a UK government-backed certification designed to help organisations protect themselves against common cyber threats. It’s required for some government contracts in the region.
Cyber Essentials is relevant for businesses of all sizes across various industries, including finance, healthcare, education and public sector organizations. While it is primarily targeted at companies operating in the United Kingdom, its principles can be applied globally to enhance cybersecurity practices.
An example of where CIS Controls and Cyber Essentials align: CIS Safeguard 7.4 (Perform Automated Application Patch Management) maps very closely to Cyber Essentials question A6.4 (Are all high-risk or critical security updates for operating systems and firmware installed within 14 days of release?).
NIS2
NIS2 (Network and Information Security Directive 2) is an EU (European Union) directive that seeks to improve cybersecurity for essential services and digital infrastructure across the region. It’s mandatory for a wide range of sectors, including energy, transport, banking, health and digital services. The directive applies to all E.U. member states and is closely aligned with the NIST framework in the U.S.
An example of where CIS Controls and NIS2 align: CIS Safeguard 5.2 (Use Unique Passwords) and CIS Safeguards 6.3/6.4/6.5 (Require MFA for Externally Exposed Applications/Remote Access/Admin Access) maps to NIS2 Article 21 (2) (j) (The Use of Multi-Factor Authentication).
ISO/IEC 27001
ISO/IEC 27001 is the globally recognised standard for information security management systems (ISMS). It outlines the necessary requirements for an effective ISMS and offers guidance for companies of all sizes and industries on establishing, implementing, maintaining and continually improving their ISMS.
Compliance with ISO/IEC 27001 shows that an organisation has implemented a system to manage data security risks and adheres to best practices and principles defined by this international standard. While it’s not a legal requirement like the General Data Protection Regulation (GDPR), it does align well with that standard.
An example of where CIS Controls and ISO/IEC 27001 align: CIS Control 2 (Establish and Maintain a Software Inventory) maps to ISO 27001 Control A5.9 (Inventory of Information and Other Associated Assets).
PCI DSS
PCI DSS (Payment Card Industry Data Security Standard) is designed for companies that accept, process, store or transmit credit card information to maintain a secure environment. It provides guidelines for organisations of any size and industry to protect cardholder data and reduce credit card fraud. Adherence to PCI DSS signifies that a business has implemented strong security measures to safeguard payment card information.
An example of where CIS Controls and PCI DSS align: CIS Safeguard 3.2 (Establish and Maintain a Data Inventory) maps to PCI DSS v4 Requirements 9.4.2 (All media with cardholder data is classified in accordance with the sensitivity of the data.) and 9.4.5.1 (Inventories of electronic media with cardholder data are conducted at least once every 12 months.)
How Pax8 can help
Work with your clients to determine which guidelines they must follow. Once you have their guidelines in order, you can use this handbook to find where they correspond to the CIS Controls.
Then, log into the new Pax8 Marketplace, where you can use Opportunity Explorer to find solutions that fit those specific Controls. This new feature is designed to help our partners find solutions that are even more specific to their clients’ needs and is built with the CIS Controls directly into the experience.
Not a partner yet? Learn about becoming a Pax8 partner here.